ISO/IEC 27005 Risk Manager training enables you to develop the competence to master the risk management process related to all assets of relevance for Information Security using the ISO/IEC 27005 standard as a reference framework. During this training course, you will also gain a thorough understanding of best practices of risk assessment methods such as OCTAVE, EBIOS, MEHARI and harmonized TRA. This training course corresponds with the implementation process of the ISMS framework presented in the ISO/IEC 27001 standard.
«The trainer was the main reason I learned something valuable; made the class entertaining and fronted good discussions.»
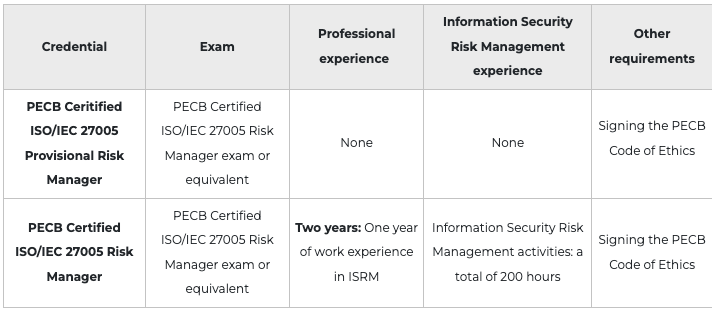
After successfully completing the exam, you can apply for the credentials shown on the table below. You will receive a certificate once you comply with all the requirements related to the selected credential. For more information about ISO/IEC 27001 certifications and the PECB certification process, please refer to the Certification Rules and Policies.
Introduction to Information Security controls as recommended by ISO/IEC 27002
Implementation of a risk management process based on ISO/IEC 27005
Overview of other Information Security risk assessment methods and Certification Exam
The exam is will take place at the end of the course on onsite classroom courses
For Virtual courses we will send out a voucher that gives you access to an online exam. This can be booked and taken home monitored by a proctor via camera. More information about the exam rules will be send from PECB
The exams an Multiple Choice exam; candidates are only authorized to use the following reference materials:
Examination rules and policies