ISO/IEC 27005 Lead Risk Manager is an advanced course designed to provide participants with in-depth knowledge and practical skills in information security risk management based on the ISO/IEC 27005 standard. The course focuses on equipping delegates with the ability to lead risk management activities, perform complex risk assessments, implement risk treatment strategies, and embed risk practices into organisational processes.
This course goes beyond basic risk concepts and delves into professional-level approaches that help organisations manage risk effectively in complex environments. Participants learn how to structure risk management frameworks, conduct detailed risk analyses, prioritise treatments, and align risk activities with business objectives and governance requirements. Real-world examples and practical exercises help bridge theory with applicable risk management practices.
 Course objectives
Course objectivesUpon completion of this course, participants will be able to:
 Prerequisites
PrerequisitesParticipants should already have a foundation in information security risk management, preferably through ISO/IEC 27005 Foundation certification or equivalent experience in risk management.
 Target audience
Target audienceThis course is designed for risk managers, security professionals with responsibility for risk governance, compliance-officers, consultants and professionals who lead or coordinate organisational risk management activities.

Participants begin with a deeper examination of the ISO/IEC 27005 standard, focusing on advanced risk concepts, key definitions and how structured risk management underpins organisational governance.
This section focuses on how to lead risk management activities, including establishing organisational context, aligning risk strategies with business goals, and creating mechanisms for high-level oversight and accountability.
Participants explore structured risk assessment approaches, including advanced identification, quantitative and qualitative analysis, and prioritisation techniques that support decision-making and resource allocation.
This part of the course addresses the selection and implementation of risk treatment options. Participants learn how to design appropriate risk controls, mitigation plans and treatment monitoring schemes to ensure continuous improvement.
Participants learn how to integrate risk management processes with other organisational management systems, including ISO/IEC 27001, to support governance and compliance frameworks.
This section covers how to monitor risk performance, conduct reviews, evaluate treatment effectiveness, and embed practices that support a continual improvement of risk posture and resilience.
The course concludes with structured preparation for the ISO/IEC 27005 Lead Risk Manager certification exam, including review of key competencies, exam structure and success strategies.

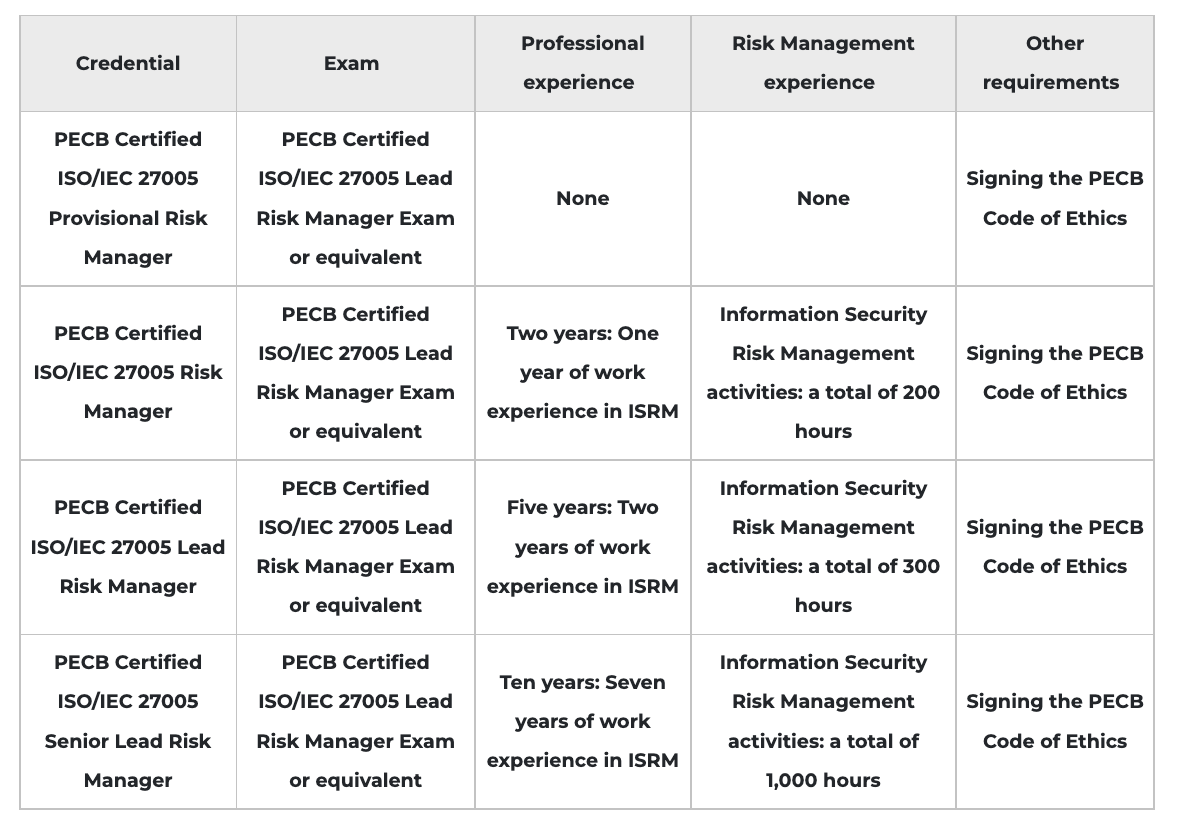
After successfully completing the exam, you can apply for the credentials shown on the table below. You will receive a certificate once you comply with all the requirements related to the selected credential. For more information about ISO/IEC 27001 certifications and the PECB certification process, please refer to the Certification Rules and Policies.
The exam is will take place at the end of the course on onsite classroom courses
For Virtual courses we will send out a voucher that gives you access to an online exam. This can be booked and taken home monitored by a proctor via camera. More information about the exam rules will be send from PECB
The exams an Multiple Choice exam; candidates are only authorized to use the following reference materials:

Duration: 5 days
Price: 27 900
Language: English
Format: Open course and corporate training
Hva lærer jeg på dette kurset?
Du lærer avanserte konsepter og teknikker innen informasjonssikkerhetsrisikostyring, inkludert ledelse av risikoaktiviteter, risikovurdering, behandling og kontinuerlig forbedring i tråd med ISO/IEC 27005.
Hva kreves for å delta?
Det anbefales at du har ISO/IEC 27005 Foundation eller tilsvarende erfaring med risikostyring før du deltar.
Hvordan gjennomføres eksamen?
Eksamen gjennomføres enten fysisk på kursstedet eller online med voucher og online eksamensvakt.
Hva skjer hvis jeg ikke består første eksamen?
Du får som regel ett nytt eksamensforsøk som tas online.
Får jeg ekstra tid på eksamen?
Ja, du får ekstra tid dersom engelsk ikke er ditt morsmål, i tråd med sertifiseringsreglene.
Hvilken sertifisering får jeg?
Etter godkjent eksamen oppnår du PECB Certified ISO/IEC 27005 Provisional Risk Manager sertifiseringen. For å få full sertifisering kan det også stilles krav til dokumentert arbeidserfaring innen informasjonssikkerhet og ISRM-arbeid. Sjekk tabellen under sertifisering for mer informasjon.
Får jeg ISO-standaren?
Nei, men du får tilgang til en lånestandar som du kan bruke under kurset og eksamen.
Hva er forskjellen på Lead Risk Manager og Foundation?
Lead Risk Manager går langt dypere inn i ledelse og anvendelse av risiko sammenlignet med Foundation som gir grunnleggende risikokonsepter.
Er dette kurset relevant for ledere?
Ja, dette kurset er relevant for ledere, risikokoordinatorer, konsulenter og fagpersoner med ansvar for risiko og styring.
Kan jeg ta dette kurset som e-læring eller selvstudium?
Nei, det er ikke mulig å ta dette kurset som e-læring, men mulig med selvstudie. Send en mail til prosjekt@glassper.no for mer informasjon og bestilling.
